Trust, but verify: the risks and rewards of vendor relationships

Partnering with a vendor opens up your business to new collaborative opportunities, but also brings new risks to the integrity of your organisation. When choosing a new supplier, what must companies do to ensure their networks and BSS/OSS remain secure and their reputations intact?
In 1987, at the signing of the Intermediate Nuclear Force treaty, Ronald Reagan shared with Mikhail Gorbachev his admiration for the saying: доверяй, но проверяй – “Trust, but verify.”
Today’s preferred weapons of mass destruction though aren’t missiles, but devastating cyberattacks targeting national infrastructure and private businesses, perpetrated by shady threat actors.
Does the current landscape render the trust but verify principle obsolete?
Hardly a week goes by without news of another major breach of some firm’s systems, leaking millions of customers’ worth of data onto the web. Increasingly, sophisticated supranational cybercrime groups and hackers are seeking to create opportunities to exploit, rather than waiting for vulnerabilities to be discovered, and communications services providers (CSPs) are frequently in the crosshairs.
For example, we’ve recently come to see the full extent of an attack on Kyivstar which knocked millions of subscribers offline for four days, caused widespread long-term damage to infrastructure, and disrupted everything from payment terminals to air raid alerts.
Наші фахівці та партнери зробили все можливе, аби відновити роботу мережі від наслідків кібератаки. 🛠
— Kyivstar (@TwiyKyivstar) December 13, 2023
🧑💻 О 18:00, наша команда розпочала включення голосового зв`язку по всій Україні. І ми неймовірно радіємо, що зв’язок починає з’являтись і ви можете зателефонувати рідним. 💙 pic.twitter.com/fsUciuLItK
Hackers broke through Kyivstar’s cybersecurity using the compromised account of one of the company’s employees via a phishing attack, according to CEO Oleksandr Komarov. Estimates put the cost of the hack at $100 million, piling pressure on a firm which is already contending with two years of conventional attacks on infrastructure.
When mass leaks of accounts and ransomware stitch-ups are almost weekly news, and when a teenager can hack into the private servers of Nvidia, Rockstar Games and Uber using nothing more than a mobile phone, an Amazon Firestick, a hotel TV, and a healthy dose of social engineering, what hope do large, monolithic businesses have of keeping their data and infrastructure secure?
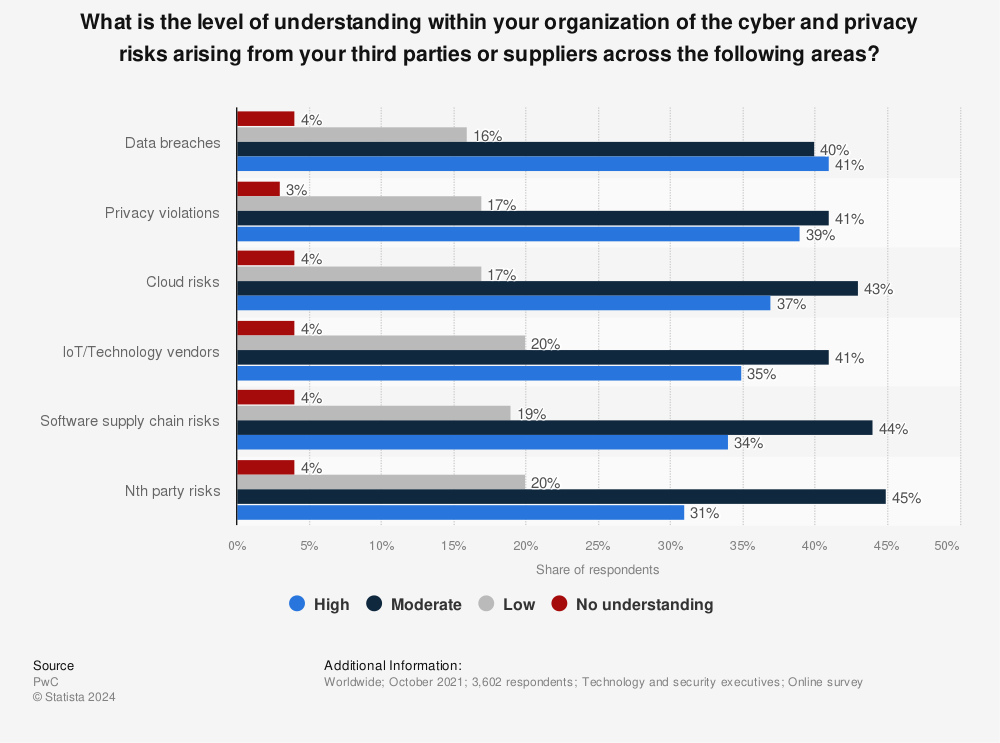
Vendor risk management is an important part of an organisation’s security management processes. Even the most capable of suppliers may bring financial, reputational or regulatory risks, so contingency planning must cover all possible scenarios and challenges that may occur. How well do you know and trust your chosen vendor?
However, nefarious actors are constantly hunting for vulnerabilities in the way suppliers are connected to their customers’ systems, looking for backdoors that could be used to steal information or install malware. Hacker groups often target individuals and businesses of interest with phishing attacks using information from LinkedIn and Facebook to pose as professional or personal contacts.
A well-defined incident response plan establishes clear roles and communication protocols for swift and effective response to security incidents. Regular compliance audits to verify that security practices align with evolving standards and legal requirements such as ISO/IEC 27001 and GDPR are absolutely imperative; ISO 28000 in particular deals with Security Management for the Supply Chain, “Identify, monitor and manage security risks throughout [the] business and supply chain.” These standards ensure vendors remain neutral, with a duty of care towards their customers.
Even after selecting a network vendor or BSS/OSS supplier, CSPs still need to manage the risks and uncertainties that may arise during the implementation and on-going support. Per NCSC guidance on cloud security, you should be confident that you understand how your data is shared with third parties, considering the entire service architecture. Implementing stringent access controls, regularly assessing and reassessing the vendor’s security posture, and conducting periodic security audits of the vendor’s systems and processes are all vital.
For every service provided by a vendor, a level of trust must be defined to ensure sustained success. As public and private organisations are increasingly reliant on suppliers to deliver sophisticated, business-critical products and services to customers, all it takes is one compromised vendor to damage their ability to operate effectively and tarnish their reputation.
Update [02/04/2024]: Last week, a Microsoft developer revealed he had discovered a backdoor in uz Utils, a popular open source data compression library, described as “the best executed supply chain attack we've seen described in the open… a nightmare scenario” by cryptography engineer Filippo Valsorda.
Cerillion has extensive experience as a secure, reliable BSS/OSS partner of leading CSPs around the world. But don’t just take our word for it – read our case studies to find out more.